http://www.globalresearch.ca/index.php?context=va&aid=17422
The Sword and the Shield: Surround Russia and China with Mobile “Missile Defense” Systems
http://www.globalresearch.ca/index.php?context=va&aid=17422
Amid War, Increasing Debt, and Cuts in Social Services: How is the Right organizing to build power in the U.S.?
What are the ramifications for the peace and social justice movements? How do these trends affect us in Hawai‘i?
The Right-Wing Populists who spawned the Tea Bag and Town Hall protests against Obama are a growing force and working to take over the Republican Party. Meanwhile, centrist Democrats are dominating the Obama Administration and dismissing populist anger at government bailouts that feed the wealthy and starve the poor.
Now, Ultra-Right activists are recruiting from among the angry Tea Bag Populists and targeting immigrants, people of color, Muslims, Arabs, reproductive rights activists, and lesbians, gays, bisexuals and transgendered persons. And they are spreading antisemitic conspiracy theories about economic woes & foreign policy.
Chip Berlet, senior analyst at Political Research Associates, has spent over 25 years studying prejudice, demonization, scapegoating, demagoguery, conspiracism, and authoritarianism. He has investigated far right hate groups, reactionary backlash movements, theocratic fundamentalism, civil liberties violations, police misconduct, government and private surveillance abuse, and other anti-democratic phenomena. He is a lively speaker defending democracy and diversity. Berlet is co–author, with Matthew N. Lyons, of Right-Wing Populism in America: Too Close for Comfort, which received a Gustavus Myers Center Award for outstanding scholarship on the subject of human rights and intolerance in North America. Berlet has appeared live on ABC’s Nightline, NBC’s Today Show, and CBS This Morning.
Sponsors: AFSC Hawai’i, World Can’t Wait Hawai’i, MANA UH Manoa chapter, Malu Aina & Truth 2 Youth.
Last night in Honolulu, Chip Berlet, senior researcher of Right wing movements for Political Research Associates and veteran organizer, spoke about the Right wing populism in the U.S. and its current resurgence in the so-called “Tea Party movement” and attacks on President Obama. He described the history of populist moments in the U.S. as volatile and unpredictable. Often these moments could tip either to the Left or the Right depending on which camp is best able to frame the message and organize legitimate anger. He cautioned that the Left dismiss or ridicule Right wing populists at their own peril. The Tea Party movement, like other populist moments, arise from real anger and insecurity about economic and social conditions. However, the Right has tapped this anger and (mis)directed it towards scapegoated groups – Jewish banking conspiracies on the one hand (elite parasites) and immigrants, gays and lesbians, Muslims, and the poor (lazy, sinful, subversive parasites). If this trend continues, he warns, conditions could get much worse, veering towards the abyss of fascism.
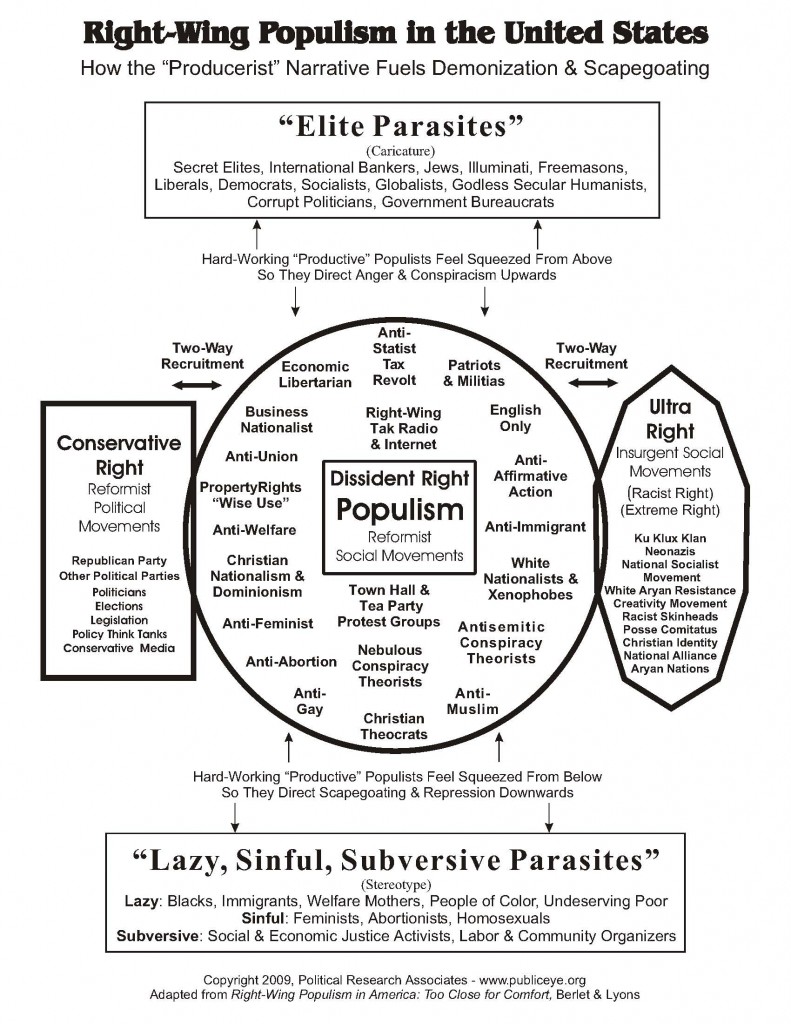 Berlet described how Right wing movements typically mobilize fears about losing some form of unfair privilege, whether it be economic, political power or social status. They turn this into a neat rhetorical trick whereby victimizer becomes victim.
Berlet described how Right wing movements typically mobilize fears about losing some form of unfair privilege, whether it be economic, political power or social status. They turn this into a neat rhetorical trick whereby victimizer becomes victim.
The solution, he challenged the audience at the Honolulu Friends Meeting House, is not to make ourselves feel morally superior by dismissing or insulting people who join these movements, which is just a form of retreat, but rather to out organize them. There is no reason why the Left should not be able to build broad coalitions and movements by taking on the real grievances of the people and directing the anger towards more just systemic change.
Regarding the Right wing attacks on Obama and Left wing disappointment, Berlet said that we should “have his back, and kick his butt.” That is challenge racist attacks on Obama, but also protest and push him on progressive issues. Berlet faults the centrist Democratic insiders that surround Obama for insulating him from the upwelling anger rather than making him take on these issues. This has isolated Obama and made him appear aloof and “out of touch” with the struggles of ordinary folk.
He told a story about important lessons from the fight to defeat the anti-gay ballot measure 9 in Oregon in 1992. A Christian right group called the Oregon Citizen’s Alliance put a constitutional amendment on the ballot to make homosexuality illegal in Oregon. Gay rights political heavyweights from national organizations did the polling and concluded that with the support of liberal urban centers of Portland and Eugene, they could defeat the ballot measure. They framed a message that amounted to “smart liberal city folk wouldn’t vote for such an ignorant and bigoted measure”. Basically, the pollsters and spin doctors were calling everyone outside of the cities ignorant red necks. This would have been a disaster. most of the state is rural and fairly culturally conservative. Such an arrogant and short sighted tactical decision would have alienated 80% of the counties and made it impossible to organize for progressive issues for decades.
Instead, progressive organizers pushed the national groups out and decided that their long term success meant organizing on principled unity between a broad coalition of groups, in other words, solidarity. This was tough because there were contradictions and prejudices against gay rights among many constituencies in the state. The organizers decided that it was better to fight in a way that built a grassroots movement based on principled unity and solidarity for the long term and possibly lose at the ballot than to pick the politically expedient tactic to win the ballot measure, but poison the political water for decades – a courageous decision and a heavy burden for the organizers to bear. Ballot Measure 9 was defeated.
Berlet said that the research shows that the best way to win people over and get them to join your group or movement is through face-to-face encounters and respectful, principled dialogue and debate. Sorry, “internet warriors”. The point is not to convert the ideologically consolidated leadership, but rather to win over the people who may have reactionary politics on some issues, but who have not yet hardened in their ideological stance.
He challenged the audience to take risks and build broad coalitions to fight for justice and peace. He shared the story of the White Rose Society to make his point. The White Rose Society was a Catholic student movement in Nazi Germany that courageously educated and organized against Nazism, fully certain that they would be defeated and most certainly killed. But they felt that morally and politically, they had no choice but to resist the fascist tide. The leaders were executed, but they inspired others to resist. And anti-fascist movements grew. The emblem of the white rose has become the international symbol of anti-fascism.
What does all this have to do with demilitarization? If Right wing populism becomes more powerful and virulent, it may one day turn the existing infrastructure and mechanisms of authoritarian rule and military power into a nightmare of state violence. One of the “first principles” of the Tea Party movement is “National Defense”, which includes endless wars, runaway military spending, torture and extraordinary rendition, warrantless spying and other attacks on civil liberties. To rephrase the famous admonition from the radical labor organizer Mother Jones, “Don’t whine, organize!”
Resources for organizers can be downloaded here: http://www.publiceye.org/movement/handouts/berlet.html
Berlet will speak twice on Hawaii island:
Monday, February 8, 2010
2 pm University of Hawai’i – Hilo, UCB115
7 – 9 pm Keaau Community Center
This is a strange story: “ACORN Pimp” James O’Keefe and three co-conspirators posed as telephone repairmen and allegedly attempted to tap Louisiana Senator Landrieu’s telephone. The silly antics of O’Keefe and his cohorts would not merit wasting any bandwidth except that three of these clowns apparently have ties to intelligence entities. The conspiracy theory blogs are eating this up, describing the plot as Israeli / CIA “black ops”. Agents or just wannabes? A new Watergate scandal? We’ll have to wait and see.
>><<
http://rawstory.com/2010/01/men-charged-attempting-bug-landrieus-office-intelligence-links/
By Sahil Kapur
Wednesday, January 27th, 2010 — 10:54 am
 WASHINGTON — Two of the three men arrested on Monday along with “ACORN pimp” James O’Keefe for “maliciously tampering” with Sen. Mary Landrieu’s (D-LA) phones in her New Orleans office have ties to the United States intelligence community.
WASHINGTON — Two of the three men arrested on Monday along with “ACORN pimp” James O’Keefe for “maliciously tampering” with Sen. Mary Landrieu’s (D-LA) phones in her New Orleans office have ties to the United States intelligence community.
The three accused by the FBI of “aiding and abetting” O’Keefe are Stan Dai, Robert Flanagan and Joseph Basel. O’Keefe is 25, and the other three are 24.
Dai’s links to the intelligence community appear to be particularly strong. He was a speaker at Georgetown University’s Central Intelligence Agency summer school program in June 2009, and is also listed as an Assistant Director at the Intelligence Community Center of Academic Excellence at Trinity in D.C.
The university’s president Patricia McGuire told The Associated Press that it promoted careers in intelligence but denied that it trains students to be spies.
The Trinity program received a “$250,000 renewable grant from the U.S. Intelligence Community” upon launching in 2004, according to its Web site. The program’s goals are stated:
The IC CAE in National Security Studies Program was established during 2005 in response to the nation’s increasing need for IC professionals who are educated and trained with the unique knowledge, skills and capabilities to carry out America’s national security objectives.
The CIA summer school packet also notes that Dai “served as the Operations Officer of a Department of Defense irregular warfare fellowship program.”
 Dai has been an undergraduate fellow with the Washington-based national security think tank Foundation for the Defense of the Democracies (FDD), according to his College Leadership Program award biography at the Phillips Foundation — as Lindsay Beyerstein first reported.
Dai has been an undergraduate fellow with the Washington-based national security think tank Foundation for the Defense of the Democracies (FDD), according to his College Leadership Program award biography at the Phillips Foundation — as Lindsay Beyerstein first reported.
FDD claims that it’s partly funded by the US State Department. Its Leadership Council and Board of Advisers comprise many high-profile conservative politicians and public figures — including former House speaker Newt Gingrich, Sen. Joseph Lieberman (I-CT), Weekly Standard editor William Kristol, Rep. Eric Cantor (R-VA), former Bush official Richard Perle and columnist Charles Krauthammer.
Dai traveled to Israel for two weeks in 2004 on an FDD-sponsored trip, the Daily Herald reported. “All expenses (room, board and travel) will be assumed by FDD,” FDD’s Web site said of its Israel program.
A host of FDD testimonials from Academic Fellows reveal that many fellows have traveled to Israel for training and field trips. The Foundation says the course includes “lectures by academics, diplomats, military and intelligence officials, and politicians from Israel, Jordan, India, Turkey and the United States.”
FDD proclaims that “Like America, Israel is at the forefront in the war on terrorism.” Further explaining its interest in Israel, FDD declares:
Both the United States and Israel are democracies, and both face the same enemy. It is this connection between Israel’s experience and the future of the United States that is the essence of the Foundation for the Defense of Democracies.
One FDD testimonial, by 2004-2005 fellow Dr. Cathal J. Nolan, highlighted the group’s bond with high-level intelligence and government officials in Israel:
The access which FDD provided to top government officials–and to academic, police, security service, and intelligence experts at the highest levels–was truly remarkable. I know of no other foundation or fellowship program which is able to provide so much top-level access and first-hand intelligence and security service information in so compact a form, or in such an intellectually stimulating environment.
The CIA and Office of Director of National Intelligence have both told Politico that despite Dai’s evident connections to the intelligence community, he never officially worked for them.
Dai’s co-conspirator Robert Flanagan is currently seeking a Master of Science degree from the Missouri State University’s (Fairfax, Virginia) Defense and Strategic Studies program, according to his LinkedIn profile (which was captured by Beyerstein before it was taken down Tuesday.)
The DSS Web site description affirms its connections to “the intelligence community”:
The program’s location also provides DSS with the opportunity to draw adjunct faculty members from the top ranks of government, the defense industry, and the intelligence community.
 The program also appears to have a close relationship with the conservative establishment. Inside Higher Ed reported in 2007 that the program’s “full-time faculty of three and its nine affiliated lecturers tend to come mainly from positions in Republican administrations and conservative-leaning institutions.”
The program also appears to have a close relationship with the conservative establishment. Inside Higher Ed reported in 2007 that the program’s “full-time faculty of three and its nine affiliated lecturers tend to come mainly from positions in Republican administrations and conservative-leaning institutions.”
It appears to be an elite program and one Facebook group bills it as ardently conservative on national security and foreign policy issues. “We Do Defense (far) Right!” it proclaims:
Are you preparing for the inevitable U.S. v. ChiCom War? Are you praying every night for the employment of Ballistic Missile Defense? Do you think nuclear weapons are important for American security? Do you think MAD is a trashy liberal theory? Are you educated by great professors with real life experience?
Then this is the place for you.
Flanagan has also blogged for the conservative Pelican Institute until as recently as this month. In one post last month, he highlighted criticisms directed at Landrieu.
Flanagan’s father, William Flanagan, is currently the acting US Attorney for Louisiana’s western district. But because Flanagan was arrested in the state’s eastern district, his father will not oversee his prosecution.
The New Orleans newspaper NOLA.com, which first broke the news, reported that “one of the four was arrested with a listening device in a car blocks from the senator’s offices.” The FBI’s affidavit noted that Flanagan and Basel were in the building with O’Keefe, and a federal law enforcement official confirmed to AP that Dai was the one in the car.
The New York Times pointed out that “[t]he [FBI] affidavit did not accuse the men of trying to tap the phones, or describe in detail what they did to the equipment.” But the optics of the situation have led to suspicions that bugging Landrieu’s phones was their intention.
Although Robert Flanagan’s Facebook page has been removed, the other three all list each other as “friends” on the social networking site.
 All four of the men arrested in the plotMonday have well-documented conservative ties, The Associated Press revealed. Three of the suspects wrote for conservative publications while in college, and Flanagan has written for the national Pelican Institute.
All four of the men arrested in the plotMonday have well-documented conservative ties, The Associated Press revealed. Three of the suspects wrote for conservative publications while in college, and Flanagan has written for the national Pelican Institute.
Flanagan’s blog, flanaganreport.com, has also been deleted, but some of its content can still be found in Google’s archives. In one post, Flanagan criticized former vice president Dick Cheney.
Joseph Basel was listed by the University of Minnesota, Morris in 2005 as one of its fifteen “College Republicans.”
The publications O’Keefe and Basel wrote for while in college allegedly received money from the nonprofit education foundation The Leadership Institute.
“Leadership Institute Vice President David Fenner said in a phone interview this morning that the group had ‘informal, above-board relationships’ with both James O’Keefe and Joseph Basel when they were college students,” Talking Points Memo reported Wednesday.
Landrieu’s office released the following statement on the incident, according to NPR:
Because the details of yesterday’s incident are part of an ongoing investigation by federal authorities, our office cannot comment at this time.
The community activist group ACORN slammed O’Keefe, who angered them after unveiling their ostensibly dodgy practices. “Couldn’t have happened to a more deserving soul,” the group posted on its Twitter feed.
The incident “is further evidence of his disregard for the law in pursuit of his extremist agenda,” ACORN CEO Bertha Lewis told AP in a statement.
Additional research provided by Ron Brynaert
http://www.stuff.co.nz/sunday-star-times/news/3257142/Spies-on-the-ground-beat-ears-in-the-sky
By NICKY HAGER – Sunday Star Times

INQUISITIVE MARLBOROUGH locals have outsmarted government attempts to keep the targets of the Waihopai spy station secret – and have discovered that it is eavesdropping on Asian satellites carrying the communications of New Zealand’s friends and trading partners in that region.
The Government Communications Security Bureau (GCSB), refuses to disclose its targets. However, one of the station’s large spherical covers (or radomes) was damaged in a 2008 anti-war protest. This left the listening antenna uncovered for 15 months, during which time people living near the base collected photographs and measurements of the uncovered satellite dish.
Their findings, along with measurements by a registered surveyor, were analysed by a former navy and police telecommunications engineer for the Sunday Star-Times, revealing the satellite dish’s targets (see below). The Kiwi spy base was pointed at various times at regions occupied by Japanese, Chinese and Russian satellites. On one day in 2009 the target was one of two Asian telecommunications satellites, one Japanese and one Vietnamese, according to the surveyor’s measurements.
Both satellites provide regional phone, data, internet and television links to private companies, individuals and government agencies in Japan, South-East Asia and down to Australia and New Zealand.
Former diplomat Terence O’Brien was not surprised by the spying on Asian targets but said New Zealand needed to sort out whether our future was in Asia or still “being shaped by influences from the North Atlantic”. “We’re supposed to be getting closer to Asia… which has a considerable influence on our future prosperity and wellbeing,” whereas spying on Asia as part of an Anglo alliance was “back in an old, comfortable North Atlantic view of the world”.
Spying on East Asian countries, and especially Japan, would be consistent with the GCSB’s long-term operations. In 2006, the Star-Times reported on a misplaced 1986 GCSB annual report found among former Prime Minister David Lange’s papers deposited in the National Archives.
The report, stamped “Top Secret Umbra”, described the GCSB’s operations, including interception of Japanese government communications, with “most of the raw data” supplied by the allied US National Security Agency (NSA) and British government communications headquarters.
The GCSB has also monitored communications by the governments of the Phillipines, Laos, and South Pacific.
The GCSB’s Waihopai station has two main listening dishes. The first, established in 1989, targets South Pacific nation communications carried by the Intelsat 701 satellite. The targets of the second dish, built in 1998, have been unknown until now. The station is part of a secret network of listening stations around the world run by the GCSB’s US, British, Canadian and Australian intelligence allies.
GCSB spokesman Hugh Wolfensohn said he could not comment on the calculations about the direction of the satellite dish, but “people are free to draw whatever conclusions they wish”.
WHAT OUR SPIES WERE LISTENING TO
The satellite dish was not fixed on one satellite, but shifted between satellites for periods of weeks or months. Measurements by local people, which were only approximate, pointed to areas of sky occupied only by Japanese, Chinese and Russian satellites.
The more accurate surveyor’s measurements revealed that on July 10, 2009, the dish was aimed at a satellite positioned above the equator, far above Indonesia. Two Asian telecommunications satellites are “parked” there: one owned by Japan’s JSAT corporation and another by Vietnam’s state-owned Post and Telecommunications Group.
A former navy and police telecommunications engineer, Lionel Hussey, of Christchurch, said that based on the surveyor’s measurements, “I would give these two satellites very high but equal probability of being under surveillance.”
Chief Reporter
WAIHOPAI SPYBASE PROTEST SATURDAY JANUARY 23rd
END NZ INVOLVEMENT IN US WARS
People from all around New Zealand will be converging on Blenheim and the super-secret Waihopai satellite interception spybase, in Marlborough, on the weekend of January 22-24. The war in Afghanistan, in which the NZ military is directly involved, has got dramatically worse and President Obama’s surge of 30,000 extra US troops will escalate it further. Already it has spread across the border into Pakistan. Hillary Clinton’s NZ visit this week is aimed at whipping America’s allies into shape and to get more troops out of the Key government, whilst simultaneously dangling a Free Trade Agreement as the “reward” – nothing has changed since Holyoake’s “guns for butter” catchcry of the Vietnam War years.
The theme of our activities, both at the spybase and in Blenheim, will be anti-war. The US says that Intelligence is the key component of all the wars that it is fighting, or planning to fight, throughout the world (Yemen is the latest target in this endless war). The Anti-Bases Campaign points out that Waihopai, an important source of intelligence for the Pentagon, is New Zealand’s most important contribution to the American war machine and it means that we New Zealanders have blood on our hands. To symbolise that, our props will include crosses, coffins and white masks.
This will be the first protest at the spybase since the April 2008 deflation of one of its domes by the Ploughshares peace activists. In solidarity with them, we will be popping white balloons at the base (and we will be at their Wellington trial, for the week starting March 8).
Waihopai, of course, is a “New Zealand” base – or so the Government says. The fact is, however, that in everything but name it is an outpost of American Intelligence – paid for by the long suffering NZ taxpayer. More than $500 million of public money has been spent on the NZ Government Communications Security Bureau (the agency which runs Waihopai) in the 22 years of Waihopai’s operation. That money could have been much better utilised on health and education, not spying on behalf of Uncle Sam.
On Saturday 23rd we will meet in Blenheim’s Seymour Square at 11 am. From there we will march through central Blenheim, with speeches at the band rotunda in the Forum.
This will be followed by a visit to the Waihopai spybase itself at 2 pm. Information will be provided on the function of the base and there will be a peaceful protest, calling for its closure. Speakers, either in Blenheim and/or the spybase, will be: Keith Locke, Green MP; John Minto, of Global Peace and Justice Auckland; and Murray Horton of ABC.
Waihopai does not operate in the national interest of New Zealand. In all but name it is a foreign spybase on NZ soil, paid for with hundreds of millions of our tax dollars, and directly involves us in America’s wars. Waihopai must be closed. (For details on Waihopai and what it does, go to our Website www.converge.org.nz/abc <http://www.converge.org.nz/abc> ).
Murray Horton,
for ABC
Anti-Bases Campaign
Box 2258, Christchurch, New Zealand
cafca@chch.planet.org.nz <mailto:cafca@chch.planet.org.nz>
www.converge.org.nz/abc <http://www.converge.org.nz/abc>
http://www.democracynow.org/2010/1/8/blackwatergate_private_military_firm_in_firestorm

Blackwater is all over the news. In the last seventy-two hours, a series of breaking developments involving the notorious private military firm have come to light, ranging from their involvement in Afghanistan and Iraq, and even Germany, as well as legal cases here at home. We speak with investigative journalist and Democracy Now! correspondent Jeremy Scahill and Rep. Jan Schakowsky (D-IL), a leading member of the House Permanent Select Committee on Intelligence and the chair of the Subcommittee on Oversight and Investigations, who is launching an investigation into why two Blackwater contractors were among the dead in the
December 30 suicide bombing at the CIA station at Forward Operating Base Chapman in Khost, Afghanistan.
Guests:
Jeremy Scahill, investigative journalist and Democracy Now! correspondent, author of the international bestseller Blackwater: The Rise of the World’s Most Powerful Mercenary Army. He is a Puffin Foundation Writing Fellow at the Nation Institute.
Rep. Jan Schakowsky (D – IL), leading member of the House Permanent Select Committee on Intelligence and the chair of the Subcommittee on Oversight and Investigations
JUAN GONZALEZ: Blackwater is all over the news. In the last seventy-two hours, a series of breaking developments involving the notorious private military firm have come to light, ranging from their involvement in Afghanistan and Iraq, and even Germany, as well as legal cases here at home.
In the latest news, two former Blackwater operatives were arrested yesterday on murder charges stemming from their alleged involvement in the shooting deaths of two Afghan civilians in Kabul in May.
The news broke just hours after it was revealed Blackwater had reached a settlement with Iraqi victims of a string of shootings, including the Nisoor Square massacre, who had sued the company for what they called “senseless slaughter.” Blackwater is reportedly paying $100,000 for each of the Iraqis killed by its forces and between $20,000 to $30,000 to each Iraqi wounded. News of the settlement came a week after a federal judge dismissed manslaughter charges against five Blackwater operatives involved in the Nisoor Square massacre that killed seventeen Iraqi civilians.
Then, on Wednesday, prosecutors in Germany announced they had launched a preliminary investigation into a report that the CIA and Blackwater had planned a secret operation in 2004 to assassinate a German citizen in Hamburg with suspected ties to al-Qaeda.
AMY GOODMAN: And last but not least, Blackwater’s continued involvement with the CIA surfaced this week when it was revealed two Blackwater contractors were among the eight dead in the December 30th suicide bombing at the CIA station in Khost, Afghanistan. Last month, the CIA announced the agency had canceled its contract with Blackwater.
Illinois Representative Jan Schakowsky, a leading member of the House Permanent Select Committee on Intelligence and the chair of the Subcommittee on Oversight and Investigations, says she’ll launch an investigation. Congress member Schakowsky joins us now on the phone from Washington, DC.
And we’re joined here in the studio by investigative journalist, Democracy Now! correspondent Jeremy Scahill, author of the international bestseller Blackwater: The Rise of the World’s Most Powerful Mercenary Army, Puffin Foundation Writing Fellow at the Nation Institute.
We welcome you both to Democracy Now! Jeremy, let’s begin with you. The piece you have in The Nation magazine says “Blackwater and the Khost Bombing: Is the CIA Deceiving Congress?” Two Blackwater operatives killed there?
JEREMY SCAHILL: My understanding is that there were two Blackwater operatives killed at this bombing—one was a former Navy Seal; the other was an Army master chief sergeant—and that there was a third Blackwater operative that was wounded in the blast, I understand from my sources.
Let’s remember here that this was the worst attack on a CIA base that we know about since the 1980s. And here you have three Blackwater guys in the center of this blast at the time. Now, we’re not sure what the role was of the Blackwater guys there. That’s what Representative Schakowsky is investigating right now. But let’s say for a moment that they were doing security, because Blackwater has, since 2002, had a contract with the CIA to do force protection in Afghanistan for the CIA. They not only guard static outposts of the CIA, but when CIA operatives move around the country, Blackwater guys travel with them as their security.
So if they were doing the security there, and you have, on their watch, this incredibly devastating attack, not just against some random CIA outpost in the middle of Canada or something, but against the epicenter of the forward operating maneuvers that the intelligence community of the US is engaged in to hunt down Ayman al-Zawahiri and Osama bin Laden, because this asset made it onto that base, we understand, claiming that he had just met with Ayman al-Zawahiri. So how is it that he walks in there with explosives? And then, I think that should be one of the things that’s investigated as Congresswoman Schakowsky takes this on.
JUAN GONZALEZ: Well, Congresswoman Schakowsky, your concerns about this latest report and what you’re hoping to look into?
REP. JAN SCHAKOWSKY: You know, regardless of what the role that the Blackwater operatives were playing in this incident, why is the CIA, why is any unit of the government, the State Department, the Department of Defense—why would anyone hire this company, which is a repeat offender, threatening the mission of the United States, threatening, endangering the lives of American, well, CIA and military, and then—and also known to threaten and kill innocent civilians? It is just amazing to me, astonishing to me, that we still find Blackwater anywhere in the employ of the United States government at any place around the world.
AMY GOODMAN: Now, during the primaries, Hillary Clinton supported a ban on Blackwater. President Obama didn’t. How does that relate to what you’re introducing now, the legislation that you’re introducing?
REP. JAN SCHAKOWSKY: Look, I’m introducing legislation called Stop Outsourcing Our Security, and the idea of that is that when we have mission-sensitive activities, inherently governmental functions in battle zones around the world, that we should have only people that bear the stamp of the United States government. And that means that that would include no private military contractors at all in those operations.
Now, look, when we have a situation where you can question whether or not these contractors can get away with murder—after all, this case against those shooters at Nisoor Square has been dismissed—hopefully that there will be another effort by the Justice Department to go after these people, because it was dismissed for prosecutorial misconduct, which is true. I think there were many mistakes made. But right now, these contractors are in a legal limbo. And so, if these individuals can get away with murder, imagine—you don’t have to imagine, you know what it does to our relations with the Iraqi government and with governments around the world. And now you’ve got a situation where Germany is asking, what were Blackwater people doing in Germany?
JUAN GONZALEZ: Well, I’d like to ask you about that, in particular, Congresswoman. Here you have a situation not just of being involved in murder, but apparently of being involved in government-sanctioned assassination attempts. And that is being, to some degree, contracted out. Forget about whether the government should be involved in such a kind of assassination attempts, but to contract out that activity? That is really astounding.
REP. JAN SCHAKOWSKY: This really is part of an ongoing investigation that I can’t talk about, but even the fact that there is that allegation, I think, gives one a picture of the degree to which Blackwater has been completely enmeshed in these secret operations. And, you know, at least the allegation that they are, I think is disturbing enough. And there is an investigation going on around activities, you know, like that.
AMY GOODMAN: Jeremy Scahill, what do you know about what happened?
JEREMY SCAHILL: Well, Erik Prince gave this interview to Vanity Fair magazine, and he gave the interview to a former CIA lawyer, Adam Ciralsky, who, himself, has had a history of doing what’s called “graymailing,” which is that you believe or you fear that the government is going to come after you in some way, and so you then leak parts of information about what it was that you were involved with, which is what Erik Prince was doing in that Vanity Fair article as a way of sort of saying to the government, “If you come after me, I’ll blow the whistle on all these things.”
One of the things, though, that came out in that article is that Erik Prince, shortly after 9/11, assembled, he claims, a team, a secret clandestine team for the CIA that trained not at any of the official CIA facilities, but at one of Erik Prince’s homes in Virginia. He trains this team, and then they deployed around the world. And they would go into countries, and, in the parlance of the intelligence community, they would go “in dark,” meaning that, in some cases, the CIA chief of station in the countries that they went into wasn’t even notified that they were going in there.
So, what Representative Schakowsky is talking about here, or, Juan, you were asking about, is that one of these operations allegedly took place in Hamburg, Germany, where a Blackwater-led team inserted inside of Germany to hunt down this man who was a Syrian-born naturalized citizen of Germany that had been alleged to have had connections with three of the 9/11 plotters. And they were doing what’s called—they were trying to find him, fix his location, and finish him off, is what they call it. And my understanding is that someone actually in government, not a Blackwater person, called off that operation, so the trigger was never pulled.
Another operation took place, we understand, inside of Dubai. And Erik Prince talks about working on covert operations inside of Syria, as well, where he was helping the Joint Special Operations Command, JSOC, the Special Forces, identify targets inside of Syria.
So all of this needs to be very deeply probed, because you have not only a situation where these hit teams are being contracted out, but the German politicians are now saying, What if the German intelligence outsourced to a private company assassination operations in New Orleans, in the United States? How would your government respond to this? So this could be a substantial diplomatic problem for the Obama administration, because the Merkel government is now starting to ask questions. Not just Green Party politicians, but today one of Angela Merkel’s biggest allies in Germany said that they’re probing it, and they want answers from Washington.
AMY GOODMAN: Congress member Schakowsky, what kind of support do you have from the White House on either of your efforts—the legislation to stop outsourcing or the investigation?
REP. JAN SCHAKOWSKY: Well, we have met with various agencies about the issue of just the outsourcing of security issues and security matters in Afghanistan and in Iraq. And I think that the thing that’s really frightening is it seems that the United States military, the United States government, doesn’t have the capacity, at least when we talk about private security contractors, to do the job and seems to think that it is—makes us more agile and nimble to be able to contract out.
My question is, how many times do we have to—does the mission have to be endangered or do people have to be killed before we understand that it is so important for us to have people who are within the standard chain of command, where the accountability mechanisms are built in, who aren’t going to go rogue on us and do things that are improper? And so, so far, what we’re finding is that even in Iraq—and Jeremy was able to turn that up—that contracts that were supposed to be terminated continued because Blackwater had a capacity that even the United States government does not have.
This is a very unwholesome, unhealthy situation. We have to build that capacity, and we have to end this relationship with companies that don’t have the same standard of transparency and accountability as those who work directly for the United States of America.
JUAN GONZALEZ: And Jeremy, what about that Iraq situation, the Nisoor Square killings? There were some settlements that Blackwater has reached with some of the victims, but not all of them. And what’s been the reaction of the Iraqi government to the acquittals of the Blackwater people?
JEREMY SCAHILL: Well, first, on the settlement that was announced yesterday, we’re talking about not just the Nisoor Square massacre, but we’re also talking about six other incidents—the shooting of bodyguards at an Iraqi TV station, the killing of three other individuals shortly before Nisoor Square. And my understanding from sources is that the victims who—the families of people who died were paid somewhere in the ballpark of $100,000, and then injuries were compensated between $20,000 and $30,000. And then there were a couple of people that got more because of the nature of their injuries. But you’re talking about Blackwater getting—they get $1.5 billion in Iraq. Ninety percent of this company’s revenue comes from the US government. For them to pay, you know, five, six million dollars is chump change. In fact, one source that’s been involved with these cases told me that Blackwater got a real bargain here. And indeed, Blackwater released a statement saying that they were pleased with it, and it allows the company to get on with its business.
But one story that people are not really looking at, the way that these guys got off on these manslaughter charges for Nisoor Square is identical to the way that Oliver North got off on the criminal charges stemming from Iran-Contra, because they were granted immunity by the State Department immediately after the shooting. And so, the prosecutors then, from the Justice Department, had to use—could not use any information from the statements that they gave, because the had been promised immunity by the State Department. Why on earth did the State Department give these guys immunity? These were the prime suspects, and you give them an immunity that generally is reserved for people that you’re trying to flip as witnesses, not the actual suspects.
But I spoke to—and this is something no one’s reported yet—I spoke to a source with direct knowledge of the US military’s official investigation of Nisoor Square, and this source told me that military investigators had determined that it was a criminal event, that it was unprovoked fire, and—and this is what the important part is—and that military investigators had determined that those men who did the shooting at Nisoor Square were not entitled to immunity under the Bremer-era Order 17 that granted immunity to contractors, because they shot unprovoked civilians, which violated the terms of their contract, and had disobeyed orders from superiors not to leave a post where they were, meaning that they were not eligible for that immunity.
And the investigators determined that the appropriate legal venue would have been in Iraq, that the Iraqis should have been allowed to go and arrest those individuals, but they were secretly ferried out of Iraq in the dead of night by the State Department and Blackwater, taken to the US, where they then got off on murder—on manslaughter charges, on the same technicality that Oliver North got off on.
AMY GOODMAN: Could they be extradited?
JEREMY SCAHILL: Well, Scott Horton, who is an international and military law expert that you interviewed last week, I talked to him about this, and the United States and Iraq do have an extradition treaty of 1934. The Status of Forces Agreement gives Iraq jurisdiction. And if they were ineligible for Order 17 immunity, then Iraq could say that the appropriate place for their trial, now that you’ve failed to do it for technical reasons, would in fact be in Iraq.
JUAN GONZALEZ: And was that military determination done before they left the country or afterwards?
JEREMY SCAHILL: No, this was—the military started investigation within less than an hour of the last bullets being fired there. They went on the scene. They gathered forensic evidence. But this was an investigation that went on for months. And so, it’s not as though the military, you know, determined it within twenty-four hours and said, “Oh, wait a minute, we have to hand these guys over to Iraqis.” It was investigators looking and carefully and meticulously documenting this incident and then saying this was improper that they were removed from the country.
AMY GOODMAN: In the settlement, which is incredibly low, $100,000 per death, did some of the Iraqi families want to pull out?
JEREMY SCAHILL: Well, first of all, there is another lawsuit. There are other Iraqis that have different legal representation. And there’s a case that’s gotten no attention yet in the state of North Carolina. The man who was perhaps the single most prominent witness to the Nisoor Square shooting, he was driving a vehicle right behind the first vehicle that the Blackwater guys shot. His nine-year-old son was shot in the head. His head exploded on a van, on his cousins and other people in the vehicle. That man has retained counsel in North Carolina and is suing. That could be a very problematic case for Blackwater, because they’re not only suing Erik Prince of Blackwater, they’re suing the individual shooters in state court in North Carolina. So that could be the one that ends up actually going to trial.
There also—you could read it in the papers—there were—some of the plaintiffs in this case were very, very disappointed in the settlement that they got and felt that $100,000 for a death is a complete injustice.
AMY GOODMAN: Finally, the latest news of the two former Blackwater operatives who were arrested on murder charges stemming from the killing of two Afghans?
JEREMY SCAHILL: Remember, these killings took place under the Obama administration. And what’s significant about this is that the men who are alleged to have murdered—these second-degree murder charges with the indictment—two Afghan civilians were there as military trainers. These weren’t security operatives. The Obama administration is dramatically expanding the US training of Afghan forces, meaning that you’re going to have more of these types of guys on the ground. So these individuals were alleged to have opened fire unprovoked on a civilian vehicle, killing two people. They weren’t even—they weren’t guarding any diplomats. They weren’t even in the country to be guarding anyone. They were there as trainers. And yet, they’re involved with this incident that has caused some significant diplomatic problems between the US and the Karzai government.
JUAN GONZALEZ: Congresswoman Schakowsky, I’d like to ask you, finally, in terms of how, in your experience and—how the military is reacting to these continual problems with Blackwater and how it’s affecting its ability to continue its mission, whether it’s in Iraq or in Afghanistan?
REP. JAN SCHAKOWSKY: Well, I think there’s a good deal of resentment, in general, toward the contractors. You know, the companies like Blackwater recruit out of the military. We train them. They take the highly skilled people, and they skim them off. They pay them a good deal more. They are indistinguishable often to the people on the ground, to the Iraqis or the Afghans, from people who are actually in the military. And yet, they conduct themselves in a much more reckless way and—often, not always. And so, I think that the military itself—I’m talking now not about necessarily the top brass, but—would appreciate the fact if the jobs were done by the military themselves, as opposed to hiring out these companies who have proven themselves to be so unreliable and dangerous.
AMY GOODMAN: We’re going to leave it there. Congress member Jan Schakowsky, leading member of the House Permanent Select Committee on Intelligence, chair of the Subcommittee on Oversight and Investigations, thanks for joining us from Washington, DC. And Jeremy Scahill, thank you so much for your work, investigative journalist, author of Blackwater: The Rise of the World’s Most Powerful Mercenary Army, and Democracy Now! correspondent.
This would be funny if it weren’t so disturbing. This AP article in the Honolulu Advertiser describes an arsenal of new weapons in the war against terrorism. They involve some very troubling invasive surveillance and screening technologies and techniques that go far beyond clothes-penetrating x-rays. Methods such as profiling and mind-reading technologies are seriously being considered. Some of these technologies are already in use or being developed in places like Israel. Precrime, here we come.
>><<
http://www.honoluluadvertiser.com/article/20100108/BREAKING/100108015?source=rss_breaking
Updated at 7:30 a.m., Friday, January 8, 2010
Associated Press
CHICAGO — A would-be terrorist tries to board a plane, bent on mass murder. As he walks through a security checkpoint, fidgeting and glancing around, a network of high-tech machines analyzes his body language and reads his mind.
Screeners pull him aside.
Tragedy is averted.
As far-fetched as that sounds, systems that aim to get inside an evildoer’s head are among the proposals floated by security experts thinking beyond the X-ray machines and metal detectors used on millions of passengers and bags each year.
Yesterday, in the wake of the Christmas Day bombing attempt over Detroit, President Barack Obama called on Homeland Security and the Energy Department to develop better screening technology, warning: “In the never-ending race to protect our country, we have to stay one step ahead of a nimble adversary.”
The ideas that have been offered by security experts for staying one step ahead include highly sophisticated sensors, more intensive interrogations of travelers by screeners trained in human behavior, and a lifting of U.S. prohibitions against profiling.
Some of the more unusual ideas are already being tested. Some aren’t being given any serious consideration. Many raise troubling questions about civil liberties. All are costly.
“Regulators need to accept that the current approach is outdated,” said Philip Baum, editor of the London-based magazine Aviation Security International. “It may have responded to the threats of the 1960s, but it doesn’t respond to the threats of the 21st century.”
Here’s a look at some of the ideas that could shape the future of airline security:
———
MIND READERS
The aim of one company that blends high technology and behavioral psychology is hinted at in its name, WeCU — as in “We See You.”
The system that Israeli-based WeCU Technologies has devised and is testing in Israel projects images onto airport screens, such as symbols associated with a certain terrorist group or some other image only a would-be terrorist would recognize, company CEO Ehud Givon said.
The logic is that people can’t help reacting, even if only subtly, to familiar images that suddenly appear in unfamiliar places. If you strolled through an airport and saw a picture of your mother, Givon explained, you couldn’t help but respond.
The reaction could be a darting of the eyes, an increased heartbeat, a nervous twitch or faster breathing, he said.
The WeCU system would use humans to do some of the observing but would rely mostly on hidden cameras or sensors that can detect a slight rise in body temperature and heart rate. Far more sensitive devices under development that can take such measurements from a distance would be incorporated later.
If the sensors picked up a suspicious reaction, the traveler could be pulled out of line for further screening.
“One by one, you can screen out from the flow of people those with specific malicious intent,” Givon said.
Some critics have expressed horror at the approach, calling it Orwellian and akin to “brain fingerprinting.”
For civil libertarians, attempting to read a person’s thoughts comes uncomfortably close to the future world depicted in the movie “Minority Report,” where a policeman played by Tom Cruise targets people for “pre-crimes,” or merely thinking about breaking the law.
———
LIE DETECTORS
One system being studied by Homeland Security is called the Future Attribute Screening Technology, or FAST, and works like a souped-up polygraph.
It would subject people pulled aside for additional screening to a battery of tests, including scans of facial movements and pupil dilation, for signs of deception. Small platforms similar to the balancing boards used in the Nintendo Wii would help detect fidgeting.
At a public demonstration of the system in Boston last year, project manager Robert Burns explained that people who harbor ill will display involuntary physiological reactions that others — such as those who are stressed out for ordinary reasons, such as being late for a plane — don’t.
The system could be made to work passively, scanning people as they walk through a security line, according to Burns.
Field testing of the system, which will cost around $20 million to develop, could begin in 2011, The Boston Globe said in a story about the demonstration. Addressing one concern of civil libertarians, Burns said the technology would delete data after each screening.
———
THE ISRAELI MODEL
Some say the U.S. should take a page from Israel’s book on security.
At Israeli airports, widely considered the most secure in the world, travelers are subjected to probing personal questions as screeners look them straight in the eye for signs of deception. Searches are meticulous, with screeners often scrutinizing every item in a bag, unfolding socks, squeezing toothpaste and flipping through books.
“All must look to Israel and learn from them. This is not a post-911 thing for them. They’ve been doing this since 1956,” said Michael Goldberg, president of New York-based IDO Security Inc., which developed a device that can scan shoes for hidden weapons while they are still on people’s feet.
Israel also employs profiling: At Ben-Gurion Airport, Jewish Israelis typically pass through smoothly, while others may be taken aside for closer interrogation or even strip searches. Another distinquishing feature of Israeli airports is that they rely on concentric security rings that start miles from terminal buildings.
Rafi Ron, the former security director at Israel’s famously tight Ben Gurion International Airport who now is a consultant for Boston’s Logan International Airport, says U.S. airports also need to be careful not to overcommit to securing passenger entry points at airports, forgetting about the rest of the field.
“Don’t invest all your efforts on the front door and leave the back door open,” Ron said.
While many experts agree the United States could adopt some Israeli methods, few believe the overall model would work here, in part because of the sheer number of large U.S. airports — around 400, versus half a dozen in Israel.
Also, the painstaking searches and interrogations would create delays that could bring U.S. air traffic to a standstill. And many Americans would find the often intrusive and intimidating Israeli approach repugnant.
———
PROFILING
Some argue that policies against profiling undermine security.
Baum, who is also managing director of Green Light Limited, a London-based aviation security company, agrees profiling based on race and religion is counterproductive and should be avoided. But he argues that a reluctance to distinguish travelers on other grounds — such as their general appearance or their mannerisms — is not only foolhardy but dangerous.
“When you see a typical family — dressed like a family, acts like a family, interacts with each other like a family … when their passport details match — then let’s get them through,” he said. “Stop wasting time that would be much better spent screening the people that we’ve got more concerns about.”
U.S. authorities prohibit profiling of passengers based on ethnicity, religion or national origin. Current procedures call for travelers to be randomly pulled out of line for further screening.
Scrutinizing 80-year-old grandmothers or students because they might be carrying school scissors can defy common sense, Baum said.
“We need to use the human brain — which is the best technology of them all,” he said.
But any move to relax prohibitions against profiling in the U.S. would surely trigger fierce resistance, including legal challenges by privacy advocates.
———
PRIVATIZATION
What if security were left to somebody other than the federal government?
Jim Harper, director of information policy studies at the Washington-based Cato Institute, a free-market-oriented think tank, says airlines should be allowed take charge of security at airports.
Especially since 9/11, the trend has been toward standardizing security procedures to ensure all airports follow the best practices. But Harper argues that decentralizing the responsibility would result in a mix of approaches — thereby making it harder for terrorists to use a single template in planning attacks.
“Passengers, too, prefer a uniform experience,” he said. “But that’s not necessarily the best security. It’s better if sometimes we take your laptop out, sometimes we’ll pat you down. Those are things that will really drive a terrorist batty — as if they’re not batty already.”
Harper concedes that privatizing airport security is probably wishful thinking, and the idea has not gotten any traction. He acknowledges it would be difficult to allay fears of gaping security holes if it were left to each airline or airport owner to decide its own approach.
“Crowdsourcing” (solving a task by appealing to a large undefined group of web users to each do a small chunk of it) is a powerful new social technology made possible by computers and the internet. However, this article from New Scientist describes how the technique could be used to covertly enlist anonymous and unwitting participants to create networks of surveillance and control.
>><<
12:42 22 December 2009 by MacGregor Campbell
Innovation is our regular column that highlights emerging technological ideas and where they may lead
When an ad hoc team of 5000 people who assembled in just two hours found 10 weather balloons hidden across the US by the Pentagon’s research agency earlier this month, it was just another demonstration of the power of crowdsourcing – solving a task by appealing to a large undefined group of web users to each do a small chunk of it.
So far crowdsourcing has been associated with well-meaning altruism, such as the creation and maintenance of Wikipedia or searching for lost aviators. But crowdsourcing of a different flavour has started to emerge.
Law enforcement officials in Texas have installed a network of CCTV cameras to monitor key areas along that state’s 1900-kilometre-long border with Mexico. To help screen the footage, a website lets anyone log in to watch a live feed from a border camera and report suspicious activity. A similar system called Internet Eyes, which pays online viewers to spot shoplifters from in-store camera feeds, is set to launch in the UK in 2010. An Iranian website is offering rewards for identifying people in photos taken during protests over June’s elections.
Some people have declared those examples chilling. Now Jonathan Zittrain, a Harvard University law professor and co-founder of the Berkman Center for Internet and Society, says the next step may be for such efforts to get web users to help out covertly.
In a recent talk, “Minds for Sale“, at the Computer History Museum in Mountain View, California, he pointed out that this could be done right away, using Amazon’s Mechanical Turk, a service that provides a platform for anyone to farm out simple tasks.
In a speculative example, Zittrain has calculated that, assuming a population in Iran of around 72 million people, it would cost around $17,000 for the government to use Mechanical Turk to identify any arbitrary person’s picture, without the users that are doing it realising the cause they have enlisted in.
The scheme would show “Turkers” a photo of a protest, or just faces extracted from one, along with five randomly chosen photos from the country’s ID card database, and asked to say whether or not there is any match.
Users would receive a few cents each time they contribute. Furthermore, Zittrain says that such a task might be made into an addictive game, similar to Google’s image labeller.
“The people making the identifications in India or the US, idly doing this on their lunch hour instead of Minesweeper, would have no idea of the implications of what they are doing,” Zittrain said in the talk. “I think people ought to know how their work is being used,” he told New Scientist.
Crowdsourcing’s power to compartmentalise and abstract away the true meaning of tasks turns human intelligence into a commodity. Zittrain’s thought experiment shows how it could potentially entice people into participating in a project that they otherwise wouldn’t support.
Wars in Iraq and Afghanistan – $943 billion
Predator Drone – $4.5 million
SkyGrabber software – $26
Watching the drone video feed live – Priceless
>><<
DECEMBER 17, 2009
http://online.wsj.com/article/SB126102247889095011.html
$26 Software Is Used to Breach Key Weapons in Iraq; Iranian Backing Suspected
By SIOBHAN GORMAN, YOCHI J. DREAZEN and AUGUST COLE
WASHINGTON — Militants in Iraq have used $26 off-the-shelf software to intercept live video feeds from U.S. Predator drones, potentially providing them with information they need to evade or monitor U.S. military operations.
Senior defense and intelligence officials said Iranian-backed insurgents intercepted the video feeds by taking advantage of an unprotected communications link in some of the remotely flown planes’ systems. Shiite fighters in Iraq used software programs such as SkyGrabber — available for as little as $25.95 on the Internet — to regularly capture drone video feeds, according to a person familiar with reports on the matter.
U.S. officials say there is no evidence that militants were able to take control of the drones or otherwise interfere with their flights. Still, the intercepts could give America’s enemies battlefield advantages by removing the element of surprise from certain missions and making it easier for insurgents to determine which roads and buildings are under U.S. surveillance.
The drone intercepts mark the emergence of a shadow cyber war within the U.S.-led conflicts overseas. They also point to a potentially serious vulnerability in Washington’s growing network of unmanned drones, which have become the American weapon of choice in both Afghanistan and Pakistan.
The Obama administration has come to rely heavily on the unmanned drones because they allow the U.S. to safely monitor and stalk insurgent targets in areas where sending American troops would be either politically untenable or too risky.
The stolen video feeds also indicate that U.S. adversaries continue to find simple ways of counteracting sophisticated American military technologies.
U.S. military personnel in Iraq discovered the problem late last year when they apprehended a Shiite militant whose laptop contained files of intercepted drone video feeds. In July, the U.S. military found pirated drone video feeds on other militant laptops, leading some officials to conclude that militant groups trained and funded by Iran were regularly intercepting feeds.
In the summer 2009 incident, the military found “days and days and hours and hours of proof” that the feeds were being intercepted and shared with multiple extremist groups, the person said. “It is part of their kit now.”
A senior defense official said that James Clapper, the Pentagon’s intelligence chief, assessed the Iraq intercepts at the direction of Defense Secretary Robert Gates and concluded they represented a shortcoming to the security of the drone network.
“There did appear to be a vulnerability,” the defense official said. “There’s been no harm done to troops or missions compromised as a result of it, but there’s an issue that we can take care of and we’re doing so.”
Senior military and intelligence officials said the U.S. was working to encrypt all of its drone video feeds from Iraq, Afghanistan and Pakistan, but said it wasn’t yet clear if the problem had been completely resolved.
Some of the most detailed evidence of intercepted feeds has been discovered in Iraq, but adversaries have also intercepted drone video feeds in Afghanistan, according to people briefed on the matter. These intercept techniques could be employed in other locations where the U.S. is using pilotless planes, such as Pakistan, Yemen and Somalia, they said.
The Pentagon is deploying record numbers of drones to Afghanistan as part of the Obama administration’s troop surge there. Lt. Gen. David Deptula, who oversees the Air Force’s unmanned aviation program, said some of the drones would employ a sophisticated new camera system called “Gorgon Stare,” which allows a single aerial vehicle to transmit back at least 10 separate video feeds simultaneously.
Gen. Deptula, speaking to reporters Wednesday, said there were inherent risks to using drones since they are remotely controlled and need to send and receive video and other data over great distances. “Those kinds of things are subject to listening and exploitation,” he said, adding the military was trying to solve the problems by better encrypting the drones’ feeds.
The potential drone vulnerability lies in an unencrypted downlink between the unmanned craft and ground control. The U.S. government has known about the flaw since the U.S. campaign in Bosnia in the 1990s, current and former officials said. But the Pentagon assumed local adversaries wouldn’t know how to exploit it, the officials said.
Last December, U.S. military personnel in Iraq discovered copies of Predator drone feeds on a laptop belonging to a Shiite militant, according to a person familiar with reports on the matter. “There was evidence this was not a one-time deal,” this person said. The U.S. accuses Iran of providing weapons, money and training to Shiite fighters in Iraq, a charge that Tehran has long denied.
The militants use programs such as SkyGrabber, from Russian company SkySoftware. Andrew Solonikov, one of the software’s developers, said he was unaware that his software could be used to intercept drone feeds. “It was developed to intercept music, photos, video, programs and other content that other users download from the Internet — no military data or other commercial data, only free legal content,” he said by email from Russia.
Officials stepped up efforts to prevent insurgents from intercepting video feeds after the July incident. The difficulty, officials said, is that adding encryption to a network that is more than a decade old involves more than placing a new piece of equipment on individual drones. Instead, many components of the network linking the drones to their operators in the U.S., Afghanistan or Pakistan have to be upgraded to handle the changes. Additional concerns remain about the vulnerability of the communications signals to electronic jamming, though there’s no evidence that has occurred, said people familiar with reports on the matter.
Predator drones are built by General Atomics Aeronautical Systems Inc. of San Diego. Some of its communications technology is proprietary, so widely used encryption systems aren’t readily compatible, said people familiar with the matter.
In an email, a spokeswoman said that for security reasons, the company couldn’t comment on “specific data link capabilities and limitations.”
Fixing the security gap would have caused delays, according to current and former military officials. It would have added to the Predator’s price. Some officials worried that adding encryption would make it harder to quickly share time-sensitive data within the U.S. military, and with allies.
“There’s a balance between pragmatics and sophistication,” said Mike Wynne, Air Force Secretary from 2005 to 2008.
The Air Force has staked its future on unmanned aerial vehicles. Drones account for 36% of the planes in the service’s proposed 2010 budget.
Today, the Air Force is buying hundreds of Reaper drones, a newer model, whose video feeds could be intercepted in much the same way as with the Predators, according to people familiar with the matter. A Reaper costs between $10 million and $12 million each and is faster and better armed than the Predator. General Atomics expects the Air Force to buy as many as 375 Reapers.
Write to Siobhan Gorman at siobhan.gorman@wsj.com, Yochi J. Dreazen at yochi.dreazen@wsj.com and August Cole at august.cole@dowjones.com